What is Information Rights Management?
Information Rights Management (IRM) is a type of digital rights management (DRM) that is specifically used to protect documents and sensitive data from being accessed by people who shouldn’t see them.
Unlike DRM, which is often used for things like songs and movies to prevent illegal copying and sharing, IRM focuses on individual documents. This is especially important in business settings where keeping information like company emails or financial details safe is critical.
Techopedia Explains Information Rights Management Meaning
Information Rights Management ensures that only individuals with authorization can access the original or altered versions of protected information. With this safeguard in place, authorized personnel can freely share or distribute data internally and externally, confident that it remains safe.
It serves various purposes:
- Upholds copyright protection;
- Safeguards intellectual property;
- Secures confidential communications;
- Prevents unauthorized access to sensitive data.
In this definition, we will discuss the importance of IRM, its main features, and how to configure your computer for IRM.
How Does Information Rights Management Work?
In essence, IRM works by:
- Assigning Access Rights: Defining who can view, edit, or share documents based on their role or identity.
- Encrypting Data: Scrambling document content so that only authorized users with the decryption key can access it.
- Applying Usage Restrictions: Limiting how a document can be used, such as prohibiting printing or editing, to ensure information stays secure even after it’s accessed.
This system integrates seamlessly with business tools like Office 365, enhancing data security without disrupting workflow.
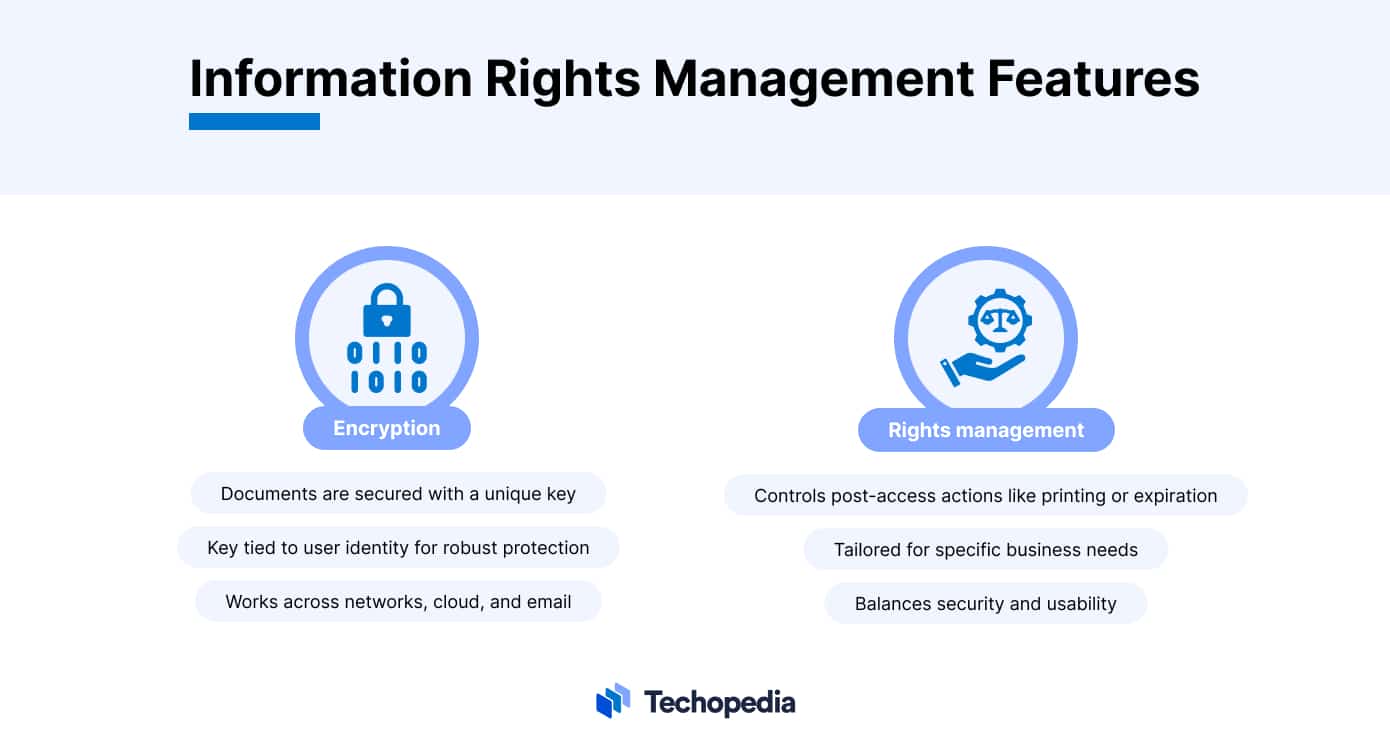
Features of Information Rights Management
IRM uses two main methods to keep documents secure: encryption and rights management.
- Encryption: This is like putting your documents in a safe that only opens with a special key. This key is usually connected to the person’s identity, ensuring that only those who are supposed to open the document can do so. This means documents can be secured no matter where they are stored – whether on a computer network, online in the cloud, or sent over email.
- Rights Management: On the other hand, controls what someone can do with a document once they’ve opened it. For example, you might be able to read a document but not print it, or the document might become unreadable after a certain date. These detailed controls are not only about blocking unauthorized access but also about adjusting document access to meet the specific needs and processes of a business.
By using both encryption and rights management, businesses can have tight control over their most sensitive data, reducing the chance of information leaks or security breaches.
For example, it can protect important company documents, like financial reports or business plans, from getting into the wrong hands. It also helps organizations follow strict privacy laws like the General Data Protection Regulation (GDPR) or Health Insurance Portability And Accountability Act (HIPAA), which require the safeguarding of personal and sensitive data.
By showing that a company can control who sees their data and what they can do with it, IRM is crucial for meeting regulatory standards, securing data, and preventing data leaks.
Information Rights Management in Office 365
Information Rights Management in Office 365 is a key part of Microsoft’s strategy for comprehensive data protection. Microsoft has integrated IRM into its cloud services to help organizations protect their most important information from unauthorized access, both from within and outside their systems.
The core of IRM Microsoft is Azure Rights Management (Azure RMS), an essential part of Microsoft Purview. Azure RMS encrypts files and emails, meaning it scrambles the data so that only people with permission can read, change, or share it. This encryption is very important for any organization that deals with confidential information, intellectual property, or any data that needs careful control.
IRM’s role in Office 365 is to make data protection a part of the everyday tools people use, like Word, Excel, PowerPoint, and Outlook. This approach makes it easier to keep documents safe and ensures that the security measures stay with the document, no matter where it’s kept or shared.
This way, organizations can secure their data not just within their own systems but also in the cloud, enhancing their overall security stance within the Office 365 environment.
Advantages and Disadvantages of IRM
Setting up IRM offers organizations a way to secure their data effectively, but it also presents several challenges. Below is a balanced overview of the advantages and disadvantages of adopting IRM.
| Aspect | Advantages | Disadvantages |
| Data Security | Stops unauthorized access or sharing. | Determined people can find a way to bypass protections. |
| Regulatory Compliance | Helps follow data protection laws. | Need more than just IRM to be fully effective. |
| Access Controls | Lets businesses control access to information. | Setting it up and dependency on specific software can be a hassle. |
| Collaboration vs. Security | Tracks who looks at or changes documents. | Too much control can slow down teamwork and productivity. |
This simplified table gives a clear view of both the positive and negative sides of IRM, showing why it’s important to implement it thoughtfully to help rather than hinder the business.
Configuring Your Computer for Information Rights Management
Setting up IRM on your computer means you need to take a few important steps.
Setting Up IRM
- Create a Microsoft Account: It is necessary to use IRM in Microsoft Office and related services.
- Update Office Programs: Ensure all your Microsoft Office applications are updated to the latest version for IRM compatibility.
- Activate Azure RMS for Organizations:
-
- A global administrator goes to the Microsoft 365 admin center.
- Select “Microsoft Purview Rights Management” and follow the prompts to activate the service across the organization.
- Global Administrator to Configure IRM Settings:
-
- Create document protection templates.
- Define access permissions for different user groups.
- Integrate IRM with SharePoint Online and Exchange Online for document and email protection.
It’s crucial for the person in charge to let the IT team and all users know about these changes and offer training or resources to help them understand how to work with IRM-protected files. This ensures everyone can adapt smoothly, keeping work flowing while boosting data security.
Protecting Documents in SharePoint Online
- Activate Azure RMS (as outlined above).
- Configure IRM in SharePoint Admin Center:
-
- Access the SharePoint admin center.
- Find the IRM settings under “Settings”.
- Choose “Use the IRM service specified in your configuration” and refresh IRM settings to enable SharePoint to apply IRM to documents.
The Bottom Line
The Information Rights Management meaning is essential to understand for businesses looking to protect sensitive data from unauthorized access.
IRM, different from DRM used for media, focuses on securing documents, which is crucial for maintaining privacy in business operations. By integrating IRM Microsoft services with Office 365, Microsoft enhances data security across cloud services through Azure RMS, encrypting files and emails so only authorized users can access them.
Despite its benefits, implementing IRM poses challenges like the need for specific software and balancing security with collaboration. Successfully managing these aspects enables organizations to safeguard sensitive information effectively, comply with privacy laws, and promote business innovation.
FAQs
What is Information Rights Management in simple terms?
What is Microsoft Information Rights Management?
How do I enable Information Rights Management?
How do I get rid of Information Rights Management in Excel?
References
- Microsoft Purview (Microsoft)