What is a Man-in-the-Middle Attack (MITM)?
A man-in-the-middle (MITM) attack is explained as a form of cyberattack in which communication between two users is monitored and modified by an unauthorized party. Generally, the attacker actively eavesdrops by intercepting a public key message exchange and retransmits the message while replacing the requested key with his own.
In the process, the two original parties appear to communicate normally. The message sender does not recognize that the receiver is an unknown attacker trying to access or modify the message before retransmitting it to the receiver. In this way, the attacker controls the entire communication.
MITM is named for a ball game where two people play catch while a third person in the middle attempts to intercept the ball. MITM is also known as a janus attack, or a fire brigade attack, a term derived from the emergency process of passing water buckets to put out a fire.

Key Takeaways
- A man-in-the-middle cyberattack is when a hacker intercepts communication between two parties to steal sensitive personal information or install malware.
- MITM attacks typically occur when a user logs in to a website or app.
- MITM attacks include Wi-Fi eavesdropping, IP, DNS or HTTPS spoofing, and session or SSL hijacking.
- Monitoring network activity for unusual disconnections and fake URLs can help detect MITM attacks.
- Ways to avoid MITM attacks include avoiding unsecured public Wi-Fi networks, enabling multi-factor authentication (MFA) and using a virtual private network and password manager.
- Show Full Guide
How Does a Man-in-the-Middle Attack Work?
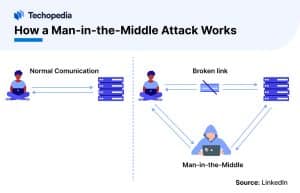
Man-in-the-middle attacks typically follow the same process, regardless of the type of attack.
- The attacker takes control of a router along a normal point of traffic.
- They redirect the Internet protocol (IP) address of the gateway they want to control to their media access control (MAC) address so that when a user makes a request, the response is sent to the attacker instead of the gateway.
In almost all cases the attacker is located on the same broadcast domain as the victim.
For instance, in a hypertext transfer protocol (HTTP) transaction, a tranmission control protocol (TCP) connection exists between client and server. The attacker splits the TCP connection into two connections – one between the victim and the attacker and the other between attacker and the server.
When intercepting the TCP connection, the attacker can read, alter, and insert data into the communication. The intruder can easily capture the session cookie, reading the HTTP header.
In an HTTPS connection, two independent secure sockets layer (SSL) connections are established over each TCP connection. An MITM attack takes advantage of the weakness in the network communication protocol, convincing the victim to route traffic through the attacker instead of a normal router, and is generally referred to as Address Resolution Protocol (ARP) spoofing.
MITM attacks frequently occur when a user logs in to a website or software. Hackers can use phishing emails to trick a user into providing their information or hijack servers to redirect traffic. Routers that use their default passwords are vulnerable to MITM attacks.
How to Detect a Man-in-the-Middle Attack
MITM attacks that use phishing or spoofing may be easy to detect if users have been trained to recognize them, but hackers are becoming increasingly sophisticated.
Signs of an MITM attack to watch out for include:
Unexpected or repeated disconnections from a website or application can indicate that an MITM attack is underway. Attackers repeatedly enter username and password combinations in an attempt to gain access to the user’s account, which can result in them being logged out by the service’s security protocols.
Cybercriminals can use connections to public Wi-Fi networks to carry out MITM attacks. They send malicious code to a user’s device to intercept messages or steal sensitive data.
Attackers can use URLs that look similar to those for legitimate websites – with perhaps only one or two characters different, which can be easy to miss. These alternate URLs deliver spoofed versions of websites to intercept users’ communications. In an MITM attack, hackers use a DNS hijack so that malicious code can collect their data.
Types of Man-in-the-Middle Attacks
There are several types of man-in-the-middle attacks that intercept users’ data.
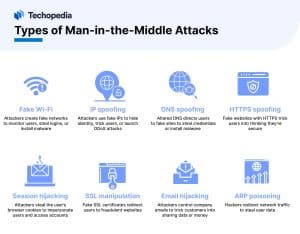
Man-in-the-Middle Attack Techniques
- Sniffing: Using devices in monitoring mode to see data that is sent to other hosts.
- Packet injection: Injecting malicious packets, or segments of data, into communication streams.
- Session hijacking: Using sniffing to identify and steal session tokens to access a user’s account.
- SSL stripping: Altering HTTPS-based address requests to force hosts to make unencrypted server requests that expose sensitive data.
Popular Man-in-the-Middle Attack Tools
Hackers make use of legitimate tools that are intended for researchers and professionals to carry out penetration testing in IT environments.
Some of the most popular software tools used in MITM attacks include:
8 Tips to Prevent Man-in-the-Middle Attacks

There are several forms of man-in-the-middle attack prevention that can help you protect your systems and personal data:
- Avoid using public Wi-Fi networks, especially if they are unsecured.
- Enable multi-factor authentication so that even if an attacker steals your login information, it cannot be used without additional authentication.
- Use a virtual private network (VPN) service to hide your IP address, create a secure connection, and encrypt your data to prevent eavesdropping.
- Use a password manager to encrypt and store all of your login credentials securely and prevent you from entering your password on a fake website.
- Use HTTPS connections and avoid URLs without HTTPS indicated in your browser. Employ DNS over HTTPS, which encrypts DNS requests to hide your activity.
- Encrypt your emails and certify them with certificates to authenticate senders and avoid an email attack.
- Educate yourself and stay up to date about the ways cyber attackers can steal your personal data. Follow zero trust (ZT) principles rather than assuming that the websites and software you use are safe.
- Use tools to monitor your network activity to guard against unusual activity and spoof website addresses.
Examples of MITM
In 2017, an MITM attack stole the personal information of 143 million people from the US credit reporting agency Equifax. Hackers exploited a critical vulnerability in the open source web application framework Apache Struts, which the company had failed to patch.
The attackers deployed a malicious Java application that appeared to be a legitimate Equifax tool. The application intercepted and manipulated customers’ data traffic in real time, stealing names, addresses, dates of birth, social security numbers, and credit card numbers. The attackers were able to move from the infected web portal to multiple servers and databases as Equifax’s systems were not segmented adequately.
In another example of a man-in-a-middle attack, in 2015, Lenovo sold computers preinstalled with Superfish adware that installed a self-signed root HTTPS certificate, enabling hackers to encrypt Web sessions and carry out HTTPS man-in-the-middle attacks. In addition, the private encryption key for the Superfish Transport Layer Security (TLS) certificate appeared to be the same for every computer, so attackers could use the key to certify malicious HTTPS websites that spoofed legitimate companies. Computers with the Superfish root certificate would then fail to flag these spoofed sites as fake.
The Bottom Line
The definition of a man-in-the-middle attack is a type of cyberattack in which a hacker intercepts communications between two systems to become the proxy between the user and the application they want to access. They redirect traffic to their own systems to monitor communications and steal users’ login credentials and personal data.
By staying up to date with the latest information on cyber security attacks, including MITM attacks, and following best practices for computer security, you can avoid having your accounts compromised.